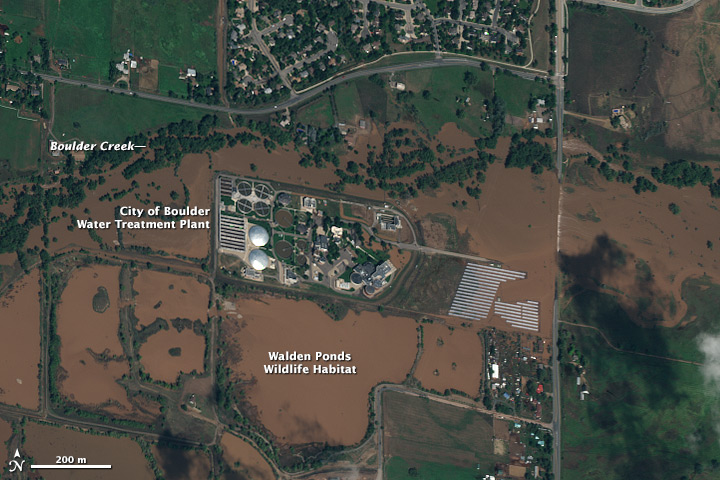
Cybersecurity is always a challenging issue for organizations, businesses, and individuals. Meanwhile, internet piracy, data theft, hacker attacks, and malicious software are increasingly unpredictable. That is why we need a Cybersecurity information security solution. includes the following component solutions:
Cyber Security Monitoring and Operation Center (SOC)
Security Operation Center SOC (Security Operation Center) is a total solution providing a full range of tools, applications, and knowledge platforms to ensure the best of today’s network security.
Cyber Security Surveillance Center functions from collecting information, analyzing information to assess security risks as well as possible risks to prevent attacks. In addition, the network security monitoring center can work in conjunction with customers to troubleshoot computers, internal network problems as well as restore the system after being attacked.
With the ability to handle very large data sources, the network security monitoring center can be a data center containing important and confidential data and ready to provide useful information for agencies and teams, needed in the fastest time.
The SOC Network Security Surveillance Center consists of many Component Centers. Each Center has its own business functions, powered by the HPC Supercomputer System, enabling efficiency when collecting and processing huge amounts of data. Include:
- Information collection centers on the Internet including the Deep Web and DarkWeb
- Center for early warning of security risks
- Center for the development of offensive and defensive tools
- Open-source security surveillance center.
Advanced malware prevention solutions
Advanced Malware Prevention is the most comprehensive solution for detecting, analyzing, and removing malicious code that exists in the system whether it is known or unknown, active or inactive. moving, …
Advanced Malware Prevention and Analysis solutions with intelligent integrated component solutions provide comprehensive system protection before, during, and after malicious code attacks:
Pre-attack protection: Malware analysis solution that allows the analysis, constantly updating information about emerging threats for early warning, enhanced defense, and defense against threats threaten.
Protection during the attack: AMP solution uses a known detection database, along with advanced malware analysis technology that enables the identification and prevention of malicious code trying to enter the system. system
Protection after being attacked: after each attack, which means that the defense system of malicious code has been penetrated, the AMP solution will monitor and analyze all activities of the malicious code. , including traffic, behavior, … to detect the origin of malicious code, thereby giving a plan to respond to the attack to minimize damage to the system.

Advanced anti-malware solution with main features:
Check and analyze data in the network
- Connect to SPAN port on network devices such as SW, Router to monitor all files exchanged over the network
- Analyze files from popular traffic streams like HTTP, FTP, SMTP, … in real-time
- Ability to handle large files
Threat classification:
- Uses Firm’s advanced technology to perform file rating and classification
- Allows checking and analyzing many types of files on Windows, Linux, Android, IOS, multimedia files, …
- Report the performance of each file on each source, destination, or file type. Check and compare files with a database of malicious files and files that can be ignored
Advanced Threats Identification, Zero Day threats
- Identify polymorphic hazards by determining functional similarity to previously known malware.
- Apply rules and regulations to all files to identify anomalies and calculate threats.
- Cyber Range System – Cyber Range
The Cyber Training system is designed to train security personnel who are responsible for protecting the organization’s critical Network resources. Cyber Training provides the infrastructure to train individuals, small or large groups in an actual network environment with legitimate network traffic and illegal traffic (generated by attackers), allows students to be exposed, and respond to a variety of problems that may be encountered on the system.
The system simulates actual network attack scenarios with different attack types, creating a variety of simulated network effects such as Data Integrity, Service Availability, and Failure exit data. The attack scripts are inserted directly into the simulated network from the attack server according to the scenarios chosen for the simulation.
The Cyber Training system provides a virtualized training environment designed to train security students, cybersecurity experts, and cybersecurity teams in protecting internal networks and military networks. , important national network systems such as Bank, Hydropower, … against threats in cyberspace. The system is designed to train cybersecurity human resources such as:
- Government Units in charge of Cyber Security
- Military and Public Security units
- Security teams for IT, IoT, SCADA, …
- Telecommunication service providers and financial and banking services
- Private businesses

Security system for ICS / SCADA automatic control networks
Security solution for ICS / SCADA automatic control networks (also known as OT network) allows customers to protect and optimize industrial control networks operating on critical infrastructures. The security platform for OT networks is designed to meet the high requirements of safety and reliability to protect OT networks such as industrial control systems, SCADA networks, IoT networks, and others.
Some main features of the system:
Automatically detect resources on the OT network and monitor network traffic, analyze traffic, apply advanced detection and analysis algorithms applied to the calibration curve to detect anomalies Usually occurring in the network can lead to a network attack or a problem in the network.
Analyze the forwarded traffic, extract a complete set of data for each system resource, and how those data are communicating in the network.
Monitor high-risk changes to the OT network. Change monitoring is combined with real-time monitoring in the OT network to reconstruct network traffic, thereby showing potentially risky changes to the system, detecting malicious commands. for critical systems (such as PLC systems).
Identify and classify behavior not present in OT networks and issue warnings when malicious behavior may occur.
Supports all types of popular protocols in use on IP networks, OT network protocols, industrial control networks, … with most of the equipment suppliers on the market such as Siemens, Mitsubishi, Schneider, Emerson, …
For detailed information about the solution, please contact: Network Security Center / C4I – Sao Vega Technology Company